4.0
Keycloak
Map groups to Lenses
Groups are case-sensitive and mapped by name with Keycloak
Integrate your user-groups with Lenses using the Keycloak group names. Create a group in Lenses using the same case-sensitive group name as in Keycloak.
For example, if the Engineers group is available in Keycloak, with Lenses assigned to it, create a group with the same name:
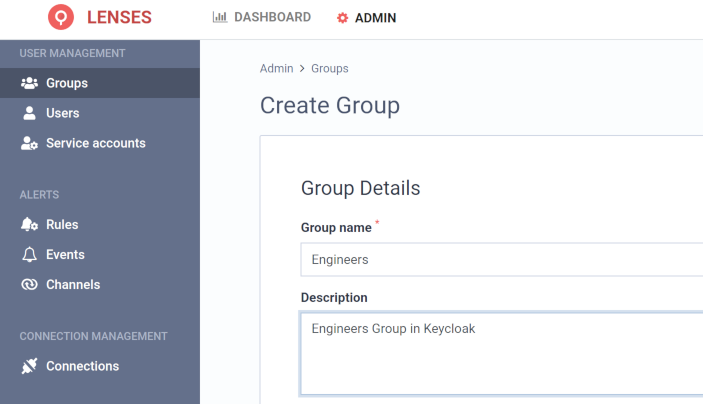
The above group will match all the users in the equivalent Keycloak group:
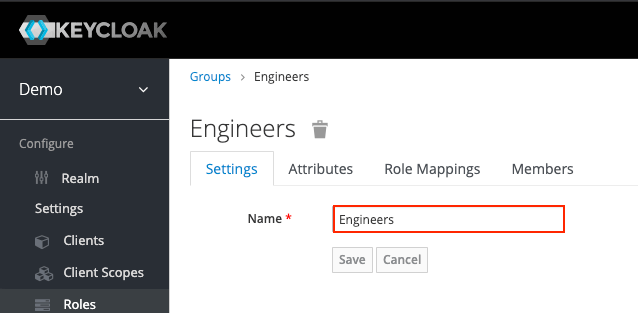
To learn how to use data centric permissions for users and service accounts check the help center .
Setup Keycloak IdP
Use Keycloak’s Administration console to create SAML applications.
Learn more about SSO with SAML in Keycloak documentation.
Create a new SAML application client
- Go to Clients
- Click Create
- Fill in the details: see table below.
- Click Save
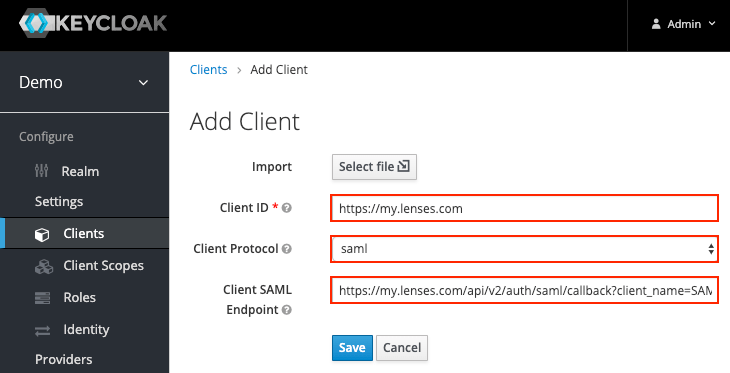
| Setting | Value |
|---|---|
| Client ID | Use the base.url of the Lenses installation e.g. https://lenses-dev.example.com |
| Client Protocol | Set it to saml |
| Client Saml Endpoint | This is the Lenses API point for Keycloak to call back. Set it to [BASE_URL]/api/v2/auth/saml/callback?client_name=SAML2Client. e.g. https://lenses-dev.example.com/api/v2/auth/saml/callback?client_name=SAML2Client |
Remember to activate HTTPS on Lenses. See TLS .
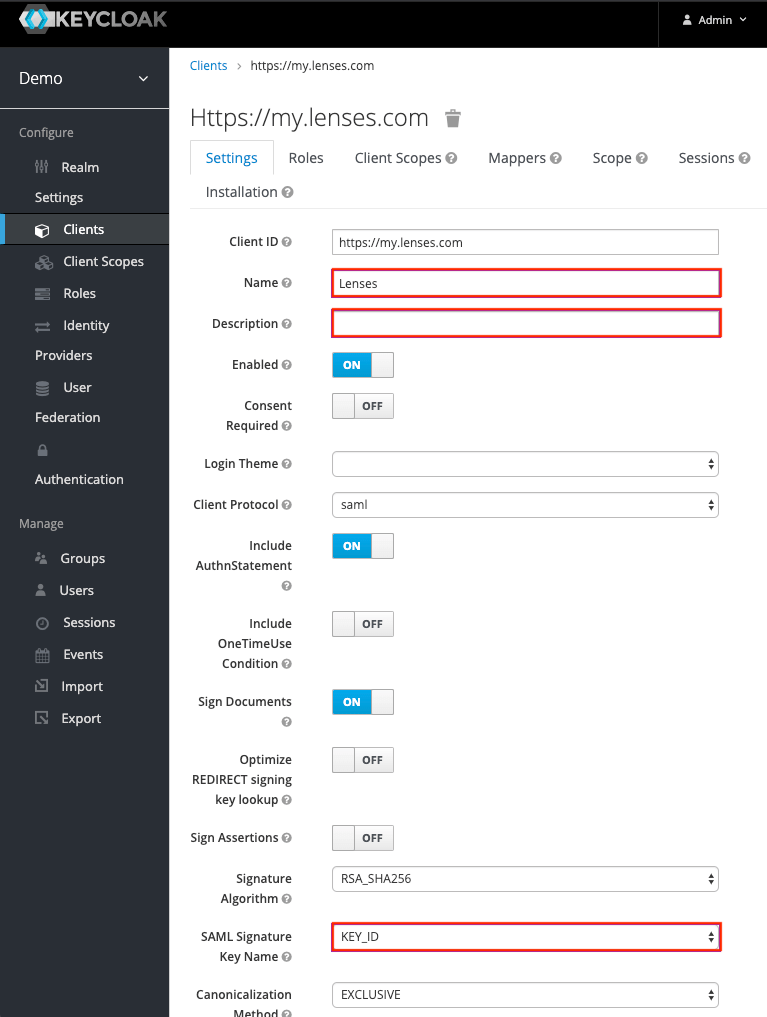
Set SAML settings
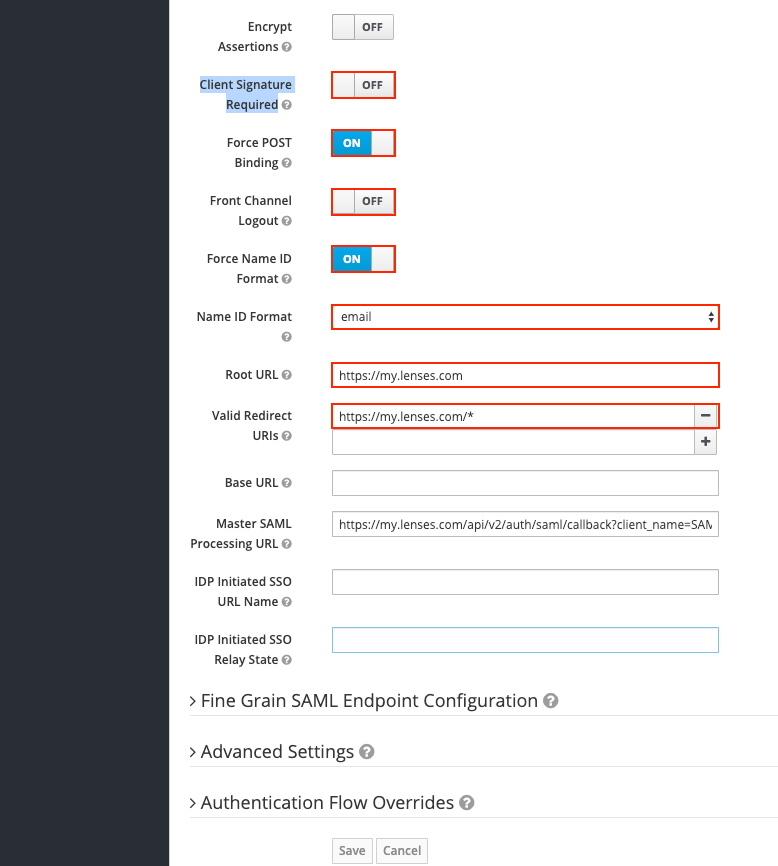
Besides the defaults already set, change the below and save:
| Setting | Value |
|---|---|
| Name | Lenses |
| Description | (Optional) Add a description to your app. |
| SAML Signature Name | KEY_ID |
| Client Signature Required | OFF |
| Force POST Binding | ON |
| Front Channel Logout | OFF |
| Force Name ID Format | ON |
| Name ID Format | email |
| Root URL | Use the base.url of the Lenses installation e.g. https://lenses-dev.example.com |
| Valid Redirect URIs | Use the base.url of the Lenses installation e.g. https://lenses-dev.example.com |
Map user groups
Configure Keycloak to communicate groups to Lenses. Head to the Mappers section.
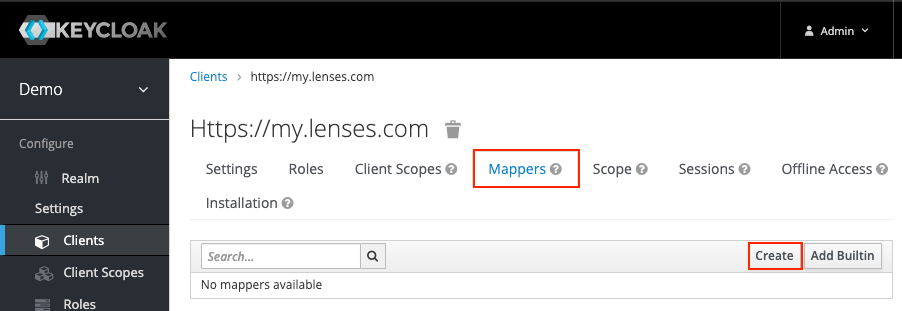
- Click Create
- Fill in the details: see table below.
- Click Save
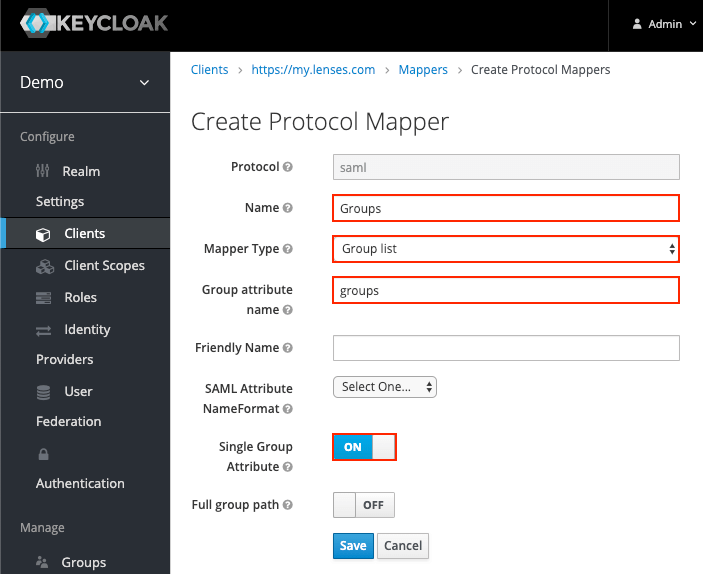
| Setting | Value |
|---|---|
| Name | Groups |
| Mapper Type | Group list |
| Group attribute name | groups (case-sensitive) |
| Single Group Attribute | ON |
| Full group path | OFF |
Download IdP XML metadata
Download the Metadata XML file with the Keycloak IdP details.
Head to the URL
This page should generate the XML metadata that you can download.
- Download from:
[KEYCLOAK_BASE_URL]/auth/realms/demo/protocol/saml/descriptore.g.https://my.keycloak.com/auth/realms/demo/protocol/saml/descriptor - You will reference this file’s path in the
security.confconfiguration file.
lenses.security.saml.idp.metadata.file="/path/to/KeycloakIDPMetadata.xml"
Configure Lenses
Given the
downloaded metadata file and a
keystore
, add
the following configuration to security.conf:
lenses.security.saml.base.url="https://lenses-dev.example.com"
lenses.security.saml.idp.provider="keycloak"
lenses.security.saml.idp.metadata.file="/path/to/KeycloakIDPMetadata.xml"
lenses.security.saml.keystore.location = "/path/to/keystore.jks"
lenses.security.saml.keystore.password = "my_keystore_password"
lenses.security.saml.key.password = "my_saml_key_password"
Keycloak SSO should now be fully activated.
See all SSO options .
