4.1
You are viewing documentation for an older version of Lenses.io View latest documentation here
Okta
Map groups to Lenses
Groups are case-sensitive and mapped by name with Okta
Integrate your user-groups with Lenses using the Okta group names. Create a group in Lenses using the same case-sensitive group name as in Okta.
For example, if the Engineers group is available in Okta, create a group with the same name:
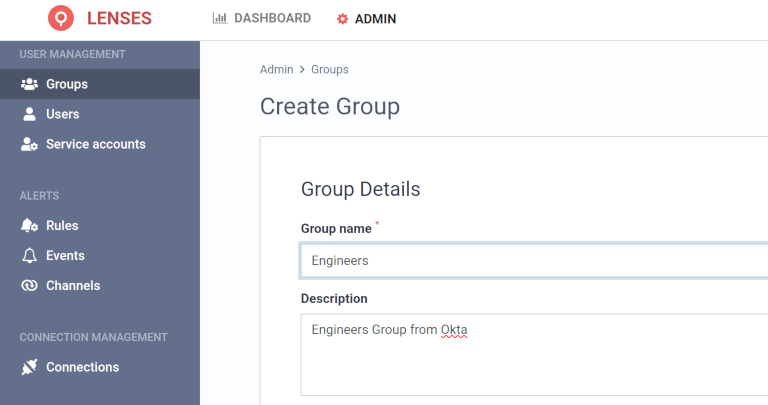
The above group will match all the users in the equivalent Okta group:
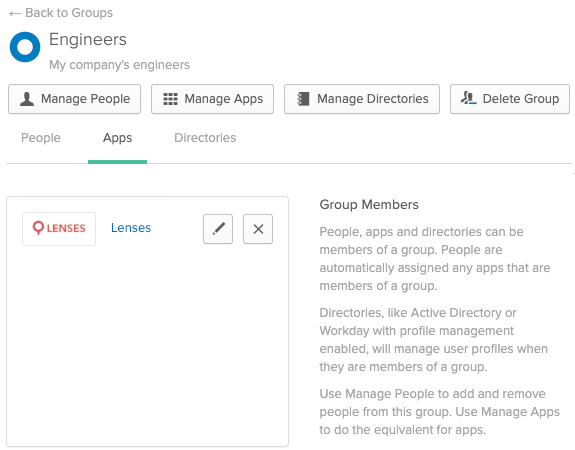
Learn how to set data permissions for users and service accounts using Apache Kafka and Okta .
Setup Okta IdP
Lenses is available directly in Okta’s Application catalog .
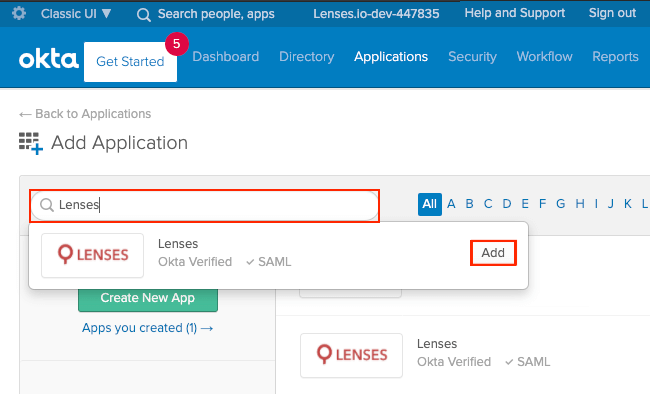
Add application in the Catalog
- Go to Applications > Applications
- Click Add Application
- Search for
Lenses - Select by pressing
Add
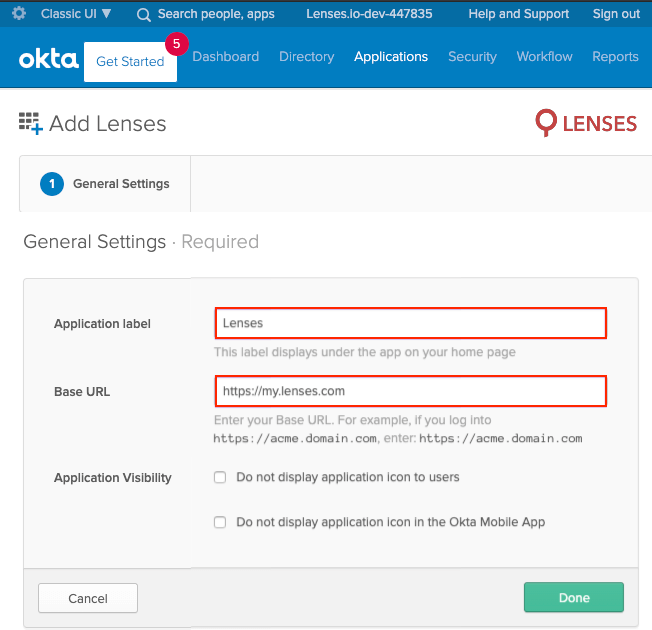
Set General Settings
- App label:
Lenses - Set the base url of your lenses installation e.g.
https://lenses-dev.example.com - Click Done
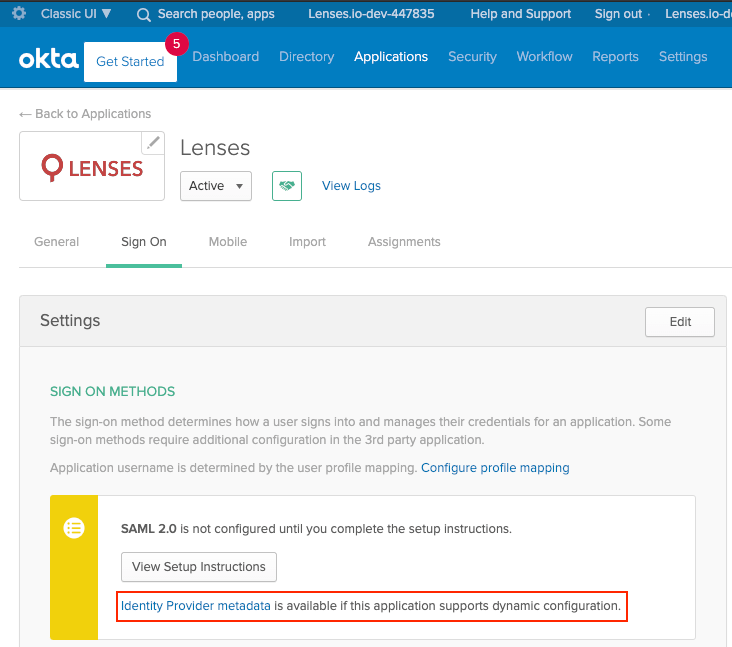
Download idP XML metadata
Download the Metadata XML file with the Okta IdP details.
- Go to Sign On > Settings > SIGN ON METHODS
- Click on Identity Provider metadata and download the XML data to a file.
- You will reference this file’s path in the
security.confconfiguration file.
lenses.security.saml.idp.metadata.file="/path/to/OktaIDPMetadata.xml"
Configure Lenses
Given the
downloaded metadata file and a
keystore
, add the
following configuration to security.conf:
lenses.security.saml.base.url="https://lenses-dev.example.com"
lenses.security.saml.idp.provider="okta"
lenses.security.saml.idp.metadata.file="/path/to/OktaIDPMetadata.xml"
lenses.security.saml.keystore.location = "/path/to/keystore.jks"
lenses.security.saml.keystore.password = "my_keystore_password"
lenses.security.saml.key.password = "my_saml_key_password"
Learn more about SSO with SAML in Okta documentation.
See all SSO options .
