4.3
Azure AD
Azure AD supports the LDAPS protocol. You can use it as an authentication provider with users, passwords and groups stored in Azure AD. When a user is authenticated successful, Lenses queries Azure AD to get the user’s groups and authorizes the user with the selected permissions.
Create a user in Azure AD who can have admin access to fetch groups and users. Here is a sample Lenses configuration:
lenses.security.ldap.url="ldaps://ldaps.lenses.io:636"
lenses.security.ldap.user="svctest@lenses.io"
lenses.security.ldap.password="<your-svc-password>"
lenses.security.ldap.base="ou=AADDC Users,dc=lenses,dc=io"
lenses.security.ldap.filter="(&(objectClass=person)(sAMAccountName=<user>))"
lenses.security.ldap.plugin.class="io.lenses.security.ldap.LdapMemberOfUserGroupPlugin"
lenses.security.ldap.plugin.group.extract.regex="(?i)CN=(\\w+),ou=AADDC Users.*"
lenses.security.ldap.plugin.memberof.key="memberOf"
lenses.security.ldap.plugin.person.name.key = "sn"
LDAP Configuration options
Create Azure AD Domain Instance
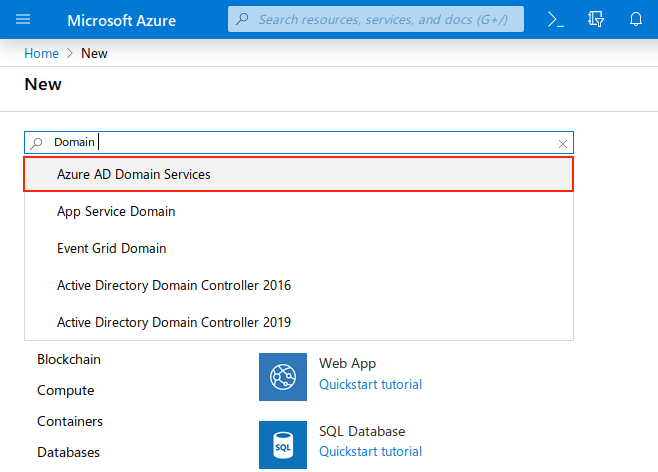
In the Azure portal create a resource. Search for Domain service and select Azure AD Domain Services from the options.
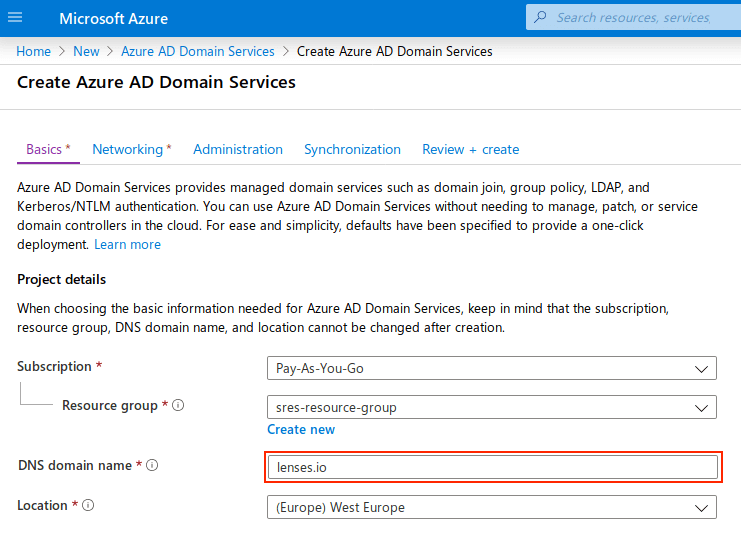
Set the DNS Domain Name as the same one you have with for your existing Azure AD tenant:
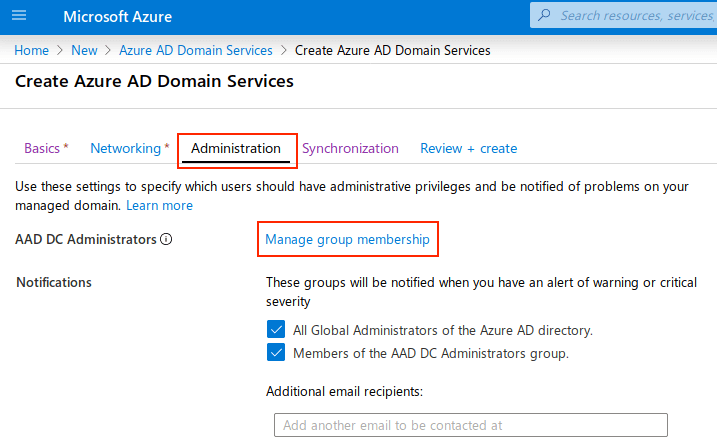
In the Administration tab you can manage the group membership for the AAD DC Administrator and control the members with access rights on Azure AD.
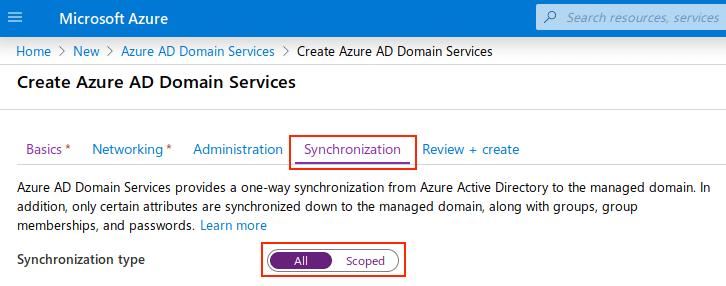
Azure AD Domain Services provides one-way synchronization from Azure Active Directory to the managed domain. Only certain attributes are synchronized to the managed domain, along with groups, group memberships and password.
The Synchronization tab provides two options. The first one is All, where everything will be synchronized to Azure AD DS managed domain. The second one is Scoped, which allows selecting specific groups to be synced.
Configure DNS server settings
Once the managed domain is ready to be used, then configure the DNS server settings for the Azure Virtual Network.
Click the button configure: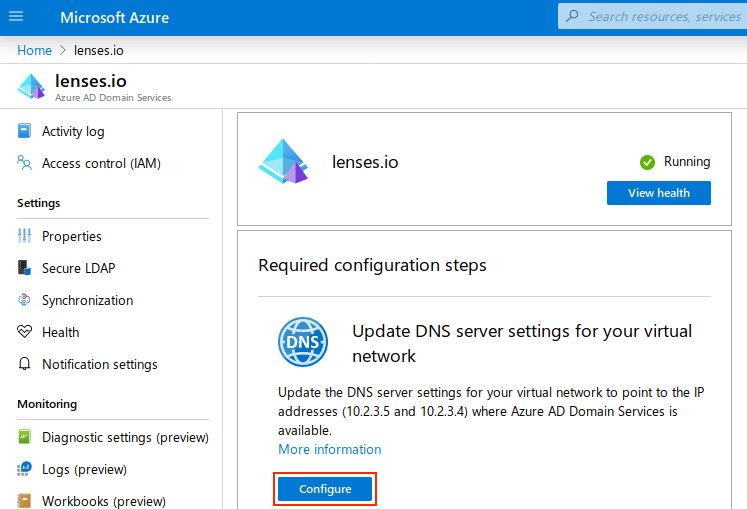
For the DNS changes to be applied, all the VMs are required to be restarted.
Azure AD DS needs password hashes in a format that’s suitable for NT LAN Manager (NTLM) and Kerberos authentication. Azure AD does not generate or store password hashes in the format that’s required for NTLM or Kerberos authentication until you enable Azure AD DS for your tenant.
For security reasons, Azure AD doesn’t store any password credentials in clear-text form. Therefore, Azure AD can’t automatically generate these NTLM or Kerberos password hashes based on users’ existing credentials.
Read the details from Microsoft on how to generate for your existing users .
Virtual network peering
The Virtual Network to deploy Lenses, requires enabling Virtual Network Peering. This allows it to communicate with Azure AD DS. You should add the IPs that has been generated on the previous step as DNS Servers.
Read more details on virtual network peering
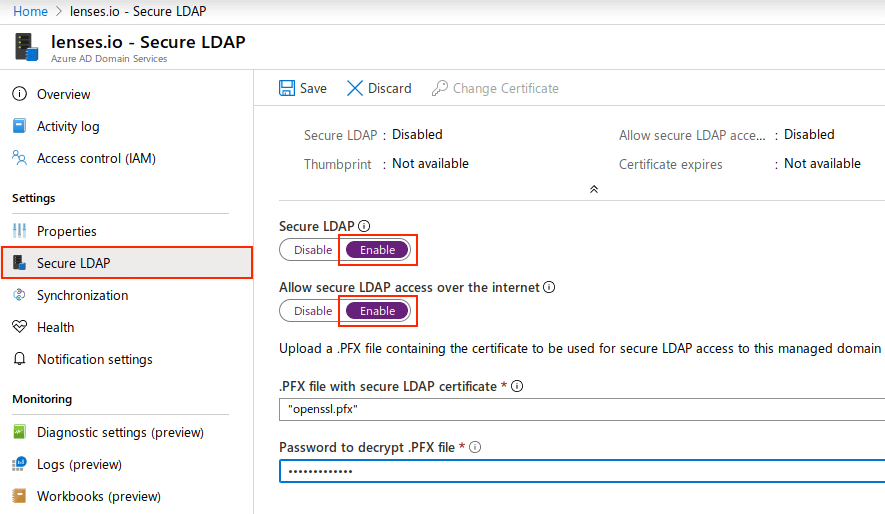
Enable Secure LDAP
To enable the LDAP(S) protocol on Azure AD DS, use the following PowerShell to generate the self-signed certificate:
# Define your DNS name used by your Azure AD DS managed domain
$dnsName="contoso.com"
# Get the current date to set a one-year expiration
$lifetime=Get-Date
# Create a self-signed certificate for use with Azure AD DS
New-SelfSignedCertificate -Subject *.$dnsName
`-NotAfter $lifetime.AddDays(365) -KeyUsage DigitalSignature, KeyEncipherment `
-Type SSLServerAuthentication -DnsName *.$dnsName, $dnsName
In case PowerShell is not available, you can use the openssl command. This following script generates a certificate for Azure AD DS.
DOMAIN="lenses.io" COUNTRY=US STATE=California ORGANIZATION="Lenses.io Ltd" ./create-certs.sh
# export certificate in PFX
openssl pkcs12 -export -name "<your-ad-domain>" -out openssl.pfx -inkey tls/my-service.key -in tls/my-service.crt
Under Secure LDAP, upload the PFX certificate and make sure the options Allow secure LDAP and access over the Internet are enabled.
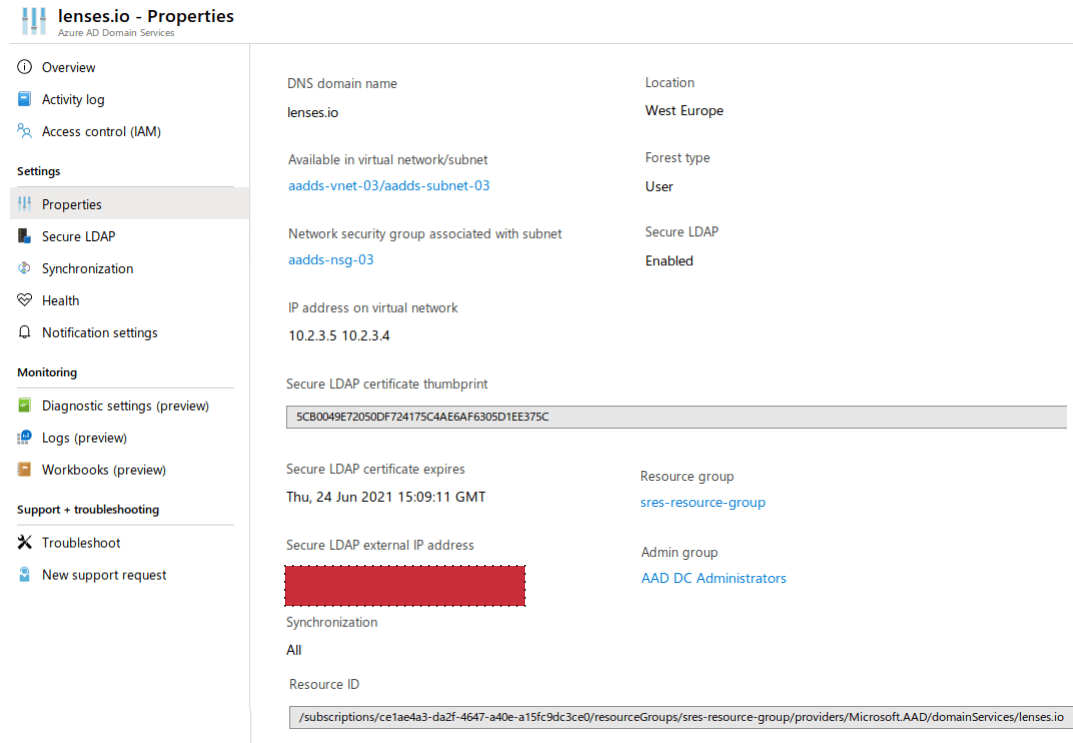
After the secure LDAP is enabled to allow secure LDAP access, use the Azure AD DS properties to review the external IP address that is used to expose the LDAP service.
Add the following to the /etc/hosts file on the virtual machine or the edge node in HDInsight cluster you want to communicate with.
<secure.ldap.ip> ldaps.<your-ad-ds-domain>
# example
50.149.72.230 ldaps.lenses.io
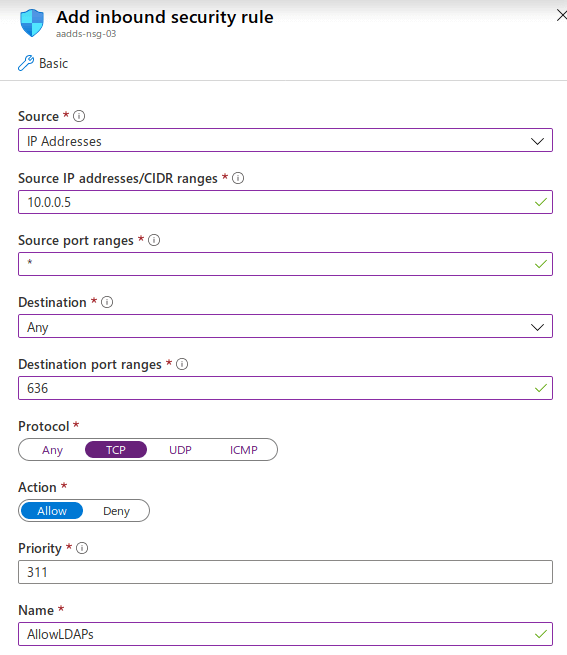
Finally, you need to allow inbound traffic to the Azure AD DS network security group for the LDAPS port 636 and limit the access only to the the virtual machine or the range of the IPs which they should have inbound access.